Why is Fibre Optic Faster
Posted by sam in Fibre Optic | 0 comments
Fibre optic cabling system is the foundation of every business network in recent times by providing connectivity between servers, computers and devices. Through the help of fibre optics, you can send messages and data from point A to point B. It allows both voice and data to be sent worldwide. Copper wires are previously used to transmit data. However, as technology continues to improve, there is a huge demand to have a faster and more advanced method of transmitting or networking. This is the reason why fibre optic cabling is fast becoming the next generations' standard data cabling. However, before you can fully understand fibre optic cabling, we need to define some important things first. For instance, what is fibre optic cable? What is Fibre Optic Cable? It is a network that contains strands of glass fibers inside an insulated casing. They carry communication signals using pulses of light. It has more capacity and is less susceptible to electrical interference compared to copper wire What are Optical Fibre? According to Wikipedia, an optical fibre is a flexible and transparent fiber made from high quality extruded glass, silica or plastic. It is slightly thicker than a human hair and can function as a waveguide or light pipe to transmit data and messages between the two ends of the fibre. Fibre Optics Fibre optics on the other hand is a technology that uses glass or plastic threads to transmit data. It is consists of a bundle of glass threads that are capable of transmitting messages through light waves. It can transmit data digitally, a natural form for computer data, rather than analogically. Now, what is fibre optic cabling? The term is based on optical fibers which are long, flexible, hair-width strands of ultra-pure glass. Optical fibre cable system is used by many companies for its speed and capability to handle large amounts of data. Aside from providing connectivity between several networks or servers, it transmits data securely, meaning no data is lost during the process while minimizing data network problems. With everything been said about optical fibre, it is quite clear that it is more promising compared to copper, especially because it’s very fast. Now that brings us back to the topic of this article, why is fibre optic faster? Why is Fibre optic faster? Fiber optic cables allow for a faster and clearer transmission of signals. Fiber optics works by transmitting signals through light waves. It is either created from glass or plastic fiber where light passes through. At the end of every fiber optics cable is a transmitter. When information or signals pass through this transmitter, it is converted to a light-emitting diode (LED) that passes through the cable. It also reaches longer distances that can span up to miles, making connection more efficient. Below are reasons why fibre optic is faster than the traditional copper cables:
- Unlike traditional copper wires that transmit electrical currents, fibre optic transmits pulses of light that are generated by light emitting diodes or laser along optical fibre. That’s one major reason, but there are more.
- Fibre optic cables have a larger-than-life kind of bandwidth, compared to the traditional copper wire.
- At very high frequency signals, copper wires will undergo loss of signal strength. However, this isn’t so for fibre optic cables. In fact, they find it convenient to carry much higher frequency ranges.
- Copper wires are more susceptible to electromagnetic interference; fibre optic technology isn’t as susceptible.
OCL’s long range Inferred Camera’s
Posted by sam in CCTV | 0 comments
Want to know how good OCL's long range Inferred Camera's are - have a look at the screen capture of a long range IR Camera recently installed. Have a look at the container at the top of the image. You can see the writing on the container. While this is not amazing in its self the container is located over 50 meters away and the area is completely pitch black. Have this technology installed in your business. https://www.youtube.com/watch?v=K_e38jb0V-4&feature=youtu.be
What is Ultra Fast Broadband? (UFB For Dummies)
Posted by sam in Fibre Optic | 0 comments

Unless you’ve been living on another planet you’ll be aware that New Zealand is currently in the process of deploying a nationwide Fibre To The Home (FTTH) network. This network is being supported by the New Zealand Government to the tune of roughly NZ$1.5 billion over the next 10 years and is being managed by Crown Fibre Holdings (CFH). Work is presently underway deploying fibre nationwide, with several thousand homes now connected to this new network. Much has been made of UFB retail pricing, and for many individuals and businesses the price they will pay for a UFB fibre connection could be significantly cheaper than existing copper or fibre connections. What does need to be understood however is the differences between fibre connection types, and pricing structures for these different services. There have been a number of public discussions in recent months (including at Nethui in July) where a number of comments made by people show a level of ignorance, both at a business and technical level, of exactly how fibre services are delivered, dimensioned, and the actual costs of providing a service. So why is UFB pricing significantly cheaper than some current fibre pricing? The answer is pretty simple – it’s all about the network architecture, bandwidth requirements and the Committed Information Rate (CIR). CIR is a figure representing the actual guaranteed bandwidth per customer, something we’ll a talk lot about later. First however, we need a quick lesson on network architecture. Current large scale fibre networks from the likes of Chorus, FX Networks, Citylink and Vector (just to name a few) are typically all Point-to-Point networks. This means the physical fibre connection to the Optical Network Terminal (ONT) on your premises is a dedicated fibre optic cable connected directly back to a single fibre port in an aggregation switch. Point-to-point architecture is similar to existing copper phone networks throughout the world, where the copper pair running to your house is dedicated connection between your premises and the local cabinet or exchange, and is used only by you. Because the fibre is only used by a single customer the speed can be guaranteed and will typically be dimensioned for a fixed speed, ie if you pay for a 100Mbps connection your connection will be provisioned with a 100Mbps CIR and this speed will be achieved 24/7 over the physical fibre connection (but once it leaves the fibre access network it is of course up to your ISP to guarantee speeds). Speeds of up to 10 Gb/s can easily be delivered over a Point-to-Point fibre connection. The core architecture of the UFB project is Gigabit Passive Optical Network (GPON). Rather than a fibre port in the Optical Line Terminal (OLT) being dedicated to a single customer, the single fibre from the port is split using a passive optical splitter so it’s capable of serving multiple customers . GPON architecture typically involves the use of 12, 24 or 32 way splitters between the OLT and the customers ONT on their premises. GPON delivers aggregate bandwidth of 2.488Gb/s downstream and 1.244 Gb/s upstream shared between all the customers who are connected to it. 24 way splitters will typically be used in New Zealand, meaning that 100Mbps downstream and 50Mbps upstream can be delivered uncontended to each customer. The difference is architecture is immediately clear – rather than the expensive cost of the fibre port having to be recovered by a single customer as is the case with a Point-to-Point network, the cost is now recovered from multiple customers. The real world result of this is an immediate drop in the wholesale port cost, meaning wholesale access can now be offered at significantly cheaper price points than is possible with a Point-to-Point architecture. GPON’s shared architecture also means that costs can be lowered even further since the architecture of a shared network means dedicated bandwidth isn’t required for every customer like is is with a Point-to-Point connection. The 2.488Gbps downstream and 1.244Gbps upstream capacity of the GPON network instantly becomes a shared resource meaning lower costs, but it can also mean a lower quality connection compared to a Point-to-Point fibre connection. Now that we’ve covered the basics of architecture we now need to learn the basics of bandwidth dimensioning. Above we learnt that a CIR is a guaranteed amount of bandwidth available over a connection. Bandwidth that isn’t guaranteed is known as an Excess Information Rate (EIR). EIR is a term to describe traffic that is best effort, with no real world guarantee of performance. The 30Mbps, 50Mbps or 100Mbps service bandwidth speeds referred to in UFB residential GPON pricing are all EIR figures, as is the norm with residential grade broadband services virtually everywhere in the world. There are is no guarantee that you will receive this EIR speed, or that the speed will not vary depending on the time of the day, or with network congestion caused by other users. With Voice Over Internet Protocol (VoIP) replacing analogue phone lines in the fibre world, guaranteed bandwidth needs to also be available to ensure that VoIP services can deliver a quality fixed line replacement. To deliver this UFB GPON residential plans also include a high priority CIR of between 2.5Mbps and 10Mbps which can be used by tagged traffic. In the real world this means that a residential GPON 100Mbps connection with a 10Mbps CIR would deliver an EIR of 100Mbps, and a guaranteed 10Mbps of bandwidth for the high priority CIR path. Those of you paying attention would have noticed a new word in the paragraph above – tagged. If you understand very little about computer networking or the internet you probably just assume that the CIR applies to the EIR figure, and that you are guaranteed 10Mbps on your 100Mbps connection. This isn’t quite the case, as maintaining a CIR and delivering a guaranteed service for high priority applications such as voice can only be done by policing traffic classes either by 801.2p tags or VLAN’s The 802.1p standard defines 8 different classes of service ranging from 0 (lowest) to 7 (highest). For traffic to use the CIR rather than EIR bandwidth it needs to be tagged with a 802.1p value within the Ethernet header so the network knows what class the traffic belongs to. Traffic with the correct high priority 802.1p tag will travel along the high priority CIR path, and traffic that either isn’t tagged, or tagged with a value other than that specified value for the high priority path will travel along the low priority EIR path. Traffic in excess of the EIR is queued, and traffic tagged with a 802.1p high priority tag that is in excess of the CIR is discarded. For those that aren't technically savvy an analogy (which is similar but not entirely correct in every aspect) is to compare your connection to a motorway. Traffic volumes at different times of the day will result in varying speeds as all traffic on the motorway is best effort, in the same way EIR traffic is best effort. To deliver guaranteed throughput without delays a high priority lane exists on the motorway that delivers guaranteed speed 24/7 to those drivers who have specially marked vehicles that are permitted to use this lane. There are probably some of you right now that are confused by the requirement for tagged traffic and two different traffic classes. The simple reality is that different Class of Service (CoS) traffic profiles are the best way to deliver a high quality end user experience and to guarantee Quality of Service (QoS) to sensitive traffic such as voice. Packet loss and jitter cause havoc for VoIP traffic, so dimensioning of a network to separate high and low priority traffic is quite simply best practice. Performance specifications exist for both traffic classes, with high priority traffic being subject to very low figures for frame delay, frame delay variation and frame loss. UFB users on business plans also have a number of different plan options that differ quite considerably to residential plans. All plans have the ability to have Priority Code Point (PCP) transparency enabled or disabled. With PCP Transparency disabled, traffic is dimensioned based on the 802.1p tag value in the same way as residential connections are. With PCP Transparency enabled, all traffic, regardless of the 802.1p tag, will be regarded as high priority and your maximum speed will be your CIR rate. As the CIR on business plans can be upgraded right up to 100Mbps, GPON can deliver a service equivalent to the performance of a Point-to-Point fibre connection. Business users also have the option of opting for a CIR on their EIR (confused yet?). This means that a 100Mbps business connection can opt for a service bandwidth of 100Mbps featuring a 2.5Mbps high priority CIR, a 95Mbps low priority EIR, and a 2.5Mbps low priority CIR. This means that at any time 2.5Mbps will be the guaranteed CIR of the combined low priority traffic. The high priority CIR can be upgraded right up to 90Mbps, with such an offering delivering a 90Mbps high priority CIR, 7.5Mbps low priority EIR, and 2.5Mbps low priority CIR. You’re now probably wondering about 802.p tagging of traffic. For upstream traffic this tagging can be done either by your router, or any network device or software application that supports this feature. Most VoIP hardware for example already comes preconfigured with 802.1p settings, however these will need to be configured with the required 802.1p value for the network. Downstream tagging of traffic introduces whole new set of challenges – while ISP’s can tag their own VoIP traffic for example, Skype traffic that may have travelled from the other side of the world is highly unlikely to contain a 802.1p tag that will place it in the high priority CIR path, so it will be treated as low priority EIR traffic. ISP’s aren’t going to necessarily have the ability to tag traffic as high priority unless it either originates within their network, or steps are taken to identify and tag specific external traffic, meaning that the uses of the CIR for downstream will be controlled by your ISP. It is also worth noting that all of the speeds mentioned in this post refer only to the physical fibre connection. Once traffic leaves the handover point, known as an Ethernet Aggregation Switch (EAS) it’s up to the individual ISP to dimension backhaul and their own upstream bandwidth to support their users. As part of their agreement with CFH, Chorus dropped their Point-to-Point fibre pricing in fibre existing areas in August 2011 to match UFB Point-to-Point pricing, which means customers currently in non UFB areas will pay exactly the same price for a Point-to-Point fibre access as they will do in a UFB area if they choose a Point-to-Point UFB connection. UFB GPON fibre plans won’t be available in existing fibre however areas until the GPON network has been deployed, either by Chorus or the LFC responsible for that area. In all UFB areas both GPON and Point-to-Point connections will ultimately be available. I hope that this explains the architecture of the UFB network, and how connection bandwidth is dimensioned. It’s not necessarily a simple concept to grasp, but with the misinformation that exists I felt it was important to attempt to write something that can hopefully be understood by the average internet user. The varying plan options and pricing options means that end users have the option of choosing the most appropriate connection type to suit their needs, whether this be a high quality business plan with a high CIR, or a lower priced residential offering that will still deliver performance vastly superior to the ADSL2+ offerings most users have today. And last but not least I have one thing to add before one or more troll(s) posts a comment saying fibre is a waste of time and complains about not getting it at their home for another 5 or 6 years. UFB is one of NZ’s largest ever infrastructure projects, and to quote the CFH website: “The Government’s objective is to accelerate the roll-out of Ultra-Fast Broadband to 75 percent of New Zealanders over ten years, concentrating in the first six years on priority broadband users such as businesses, schools and health services, plus green field
OCL have been awarded the top contractor for UFB installations
Posted by sam in Uncategorized | 0 comments

 Once again OCL have been awarded the top contractor for UFB installations in the greater Auckland / North Auckland region.
This award is based on several factors including:
Once again OCL have been awarded the top contractor for UFB installations in the greater Auckland / North Auckland region.
This award is based on several factors including:
- Quality and minimal rework
- Ease of “doing business” with
- Meeting compliance standards
- Commitment to Health and Safety
- Meeting Deadlines and project dates
- “Owing the job” and taking responsibility for outcomes
Beware of Your Telco Provider – Fraudulent Activity in Auckland
Posted by sam in Cloud Communications | 0 comments

Article By: Blair Ensor and Tony Wall | Sunday Star Times
Recently, Blair Ensor and Tony Wall of the Sunday Star Times produced an article in fraudulent activity within the telco-industry in Australia. In their revealing piece, they note that “Takeaway shops, homeware suppliers, taxi operators, recruitment firms. Small businesses with little in common except one thing – they fell for the charms of smooth-talking telco salesmen and have come to regret it.” Its now become apparent that many customers, of whom thought they were being sold a “bundled telco deal, we’re in fact entering into an a agreement with a finance company. According to Australia’s Competition and Consumer Commission, 28 similar cases have been reported, and now we’re starting to see similar cases occur in Auckland. Just recently,Intagr8 has been reported for its sales tactic used to sign up customers on Auckland’s North Shore. According to Ensor & Wall “The investigation found a number of Intagr8 customers who claimed they were unaware of the true cost of the equipment and were confused about signing two contracts – one with Intagr8 and another with a finance company. Some also claimed they were given the impression the equipment was free. Dozens of customers whom had no idea that they were locked into five-year deals with financiers. Some are now being threatened with legal action by the financiers for non-payment of bills. Firms also complained that salespeople were pushy, equipment was slow in arriving, faults weren't fixed promptly and phone bills were sometimes greater than expected. Intagr8 strongly denied the allegations and claimed competitors were spreading disinformation. In a statement through its lawyer, Warren Butterworth, the company said the vast majority of its customers were happy and more than 70 per cent renewed their contracts. Customers were fully aware of the finance component of the deal, he said, because they signed finance company documents and the specific financier was also highlighted in additional material.” "Intagr8's sales staff are ...forbidden from making false representations," the statement said, noting that the telco had an "exhaustive quality assurance process". Butterworth acknowledged a number of complaints to both the company and the Commerce Commission, but blamed the problems on an "orchestrated" campaign. "One of those sales people in particular has left the company (along with general staff occupying senior positions) and set up a business in opposition. It has been discovered since that time Intagr8's strict selling protocol has not been complied with." Intagr8 was taking court action against the former salesman and his new company, claiming damages."Intagr8's problems with any sales staff when discovered is dealt with promptly. The number of complaints are a very small percentage of total sales. At times Intagr8, as in any supplier of services and products, has to make amends to its customers but this is rarely necessary. The Commerce Commission confirmed it had launched an investigation into Intagr8 under the Fair Trading Act in 2012 following customer complaints. On that occasion the commission issued a letter of compliance advice, saying it had concerns Intagr8 salespeople "may not be clearly and sufficiently disclosing the full cost of the bundled product that they are offering". A commission spokesman said more complaints about the company surfaced last year and a new investigation had begun. Intagr8 was co-operating. An industry source with close knowledge of the business model said the modus operandi was to saturate an area and sign up as many customers as possible. "They get the finance up front, finance everything in a little magic deal, grab the cash and move on to the next one," the source said. Customers carried all the risk – if the telco went out of business, they'd be left with no phone lines, over-valued equipment, and finance company contracts they couldn't get out of. Intagr8's website says it uses equity in a customer's call spend to off-set the cost of new phone and office equipment. There is no mention of finance companies, although it does refer to equipment rental. Phone equipment supplied by Intagr8 and priced at $14,400 over five years was priced by another communications company at $3770 retail. A package priced at $9725 was charged at $51,060 by Intagr8.
Intagr8 denied its hardware was overpriced, saying the products and services it provided were in line with other equipment businesses.
Jay Marshall, of homeware importer EW Sinton, described his dealings with Intagr8 as the worst business experience he'd ever had. He thought the structure of the deals was confusing.
"They make out it's your hardware, but they're getting paid up front for all your projected calling over five years."
UDC Finance, owned by ANZ, declined to comment when asked about Intagr8's business model, the price of its equipment and whether they were aware of customer complaints. .
Joe Duncan, chief executive of finance company Advaro, said they took steps to ensure Intagr8 disclosed sufficient information to its customers and recorded phone calls to ensure people understood what they were getting into.
He said Advaro knew of complaints but thought they'd been resolved. "We are seeking clarification on this."
Grant Maud of Telecom Rentals (now TRL) said they were concerned by the allegations.
Geoff Hamilton of Equipment Finance refused to comment without Intagr8's permission.
She believed she was fired without explanation because she "told them what they didn't want to hear" about their sales techniques.
"If they can keep convincing people to buy the stuff, they'll just keep making money", she said.
Paula Pickles quit her account manager's job at Intagr8 in November after becoming concerned about the way it was operating.
She said salespeople didn't say goods were free but, on the other hand, there was no mention of a finance company.
"People didn't really understand they were signing into a finance agreement – that was my impression."
Another former employee, a technician, said he quit after about two years because he was sick of dealing with angry customers.
"For a communications company there was no communication. It just sucked."
The man, who asked not to be named, said he would often turn up to install phone systems and clients would be furious because they had not received equipment they were already paying for.
Intagr8 said in a statement if customers had issues they should get in touch. "We offer them our assurance that we will make every attempt to remedy any issue they may have."
THE CUSTOMERS
Accroding to Ensor & Wall (2015) "A free computer wasn't enough to entice Crown Cabs owner Khalil Tajek to leave Telecom, but when Intagr8 offered to throw in a "free" printer as well, that sealed it. A year later, Tajek was complaining to the Commerce Commission. He said his agreement was for a monthly bill of $250 plus GST over four years, with that amount given back to him as "credits" to offset the equipment. Shortly after receiving the hardware Tajek got a call from a man at UDC. He said that was the first he knew the gear was on finance.
"The [salesman] did not tell me about this. He just told me to sign some documents, but I did not read them and he did not leave a copy." In the following months, Tajek said, his monthly bills climbed to about $500 as his "credits" only partly offset the finance repayments. Intagr8 said there was no fixed amount for telephone charges – it depended upon usage. Busier periods would result in additional charges. The directors of EW Sinton, a homeware importer, say they effectively lost $50,000 after a "nightmare" experience with Intagr8.They knew a finance company was involved, but say Intagr8 simply failed to deliver what it promised, the equipment not working properly even when they paid more money to get it sorted.Eventually, desperate to escape the problem, they went back to their old phone provider but continued to make their monthly payments on the Intagr8 equipment."
"We were spending so much time on it, we just said 'stuff it' and went to another phone company," said managing director Phil Sinton. "We let the [Intagr8] contract run its course, it cost us about $50,000, basically for nothing."
Haider Shakib, who owns My Auto Tech in Manurewa, remembers the smooth-talking Intagr8 salesmen who arrived in a nice car.
Shakib claimed he was promised "free" phone calls if he bought equipment. He claimed he was told there was no finance component to the five-year deal.
However, monthly letters from a finance company asking for $230 began arriving. He also had to pay Intagr8 an increasingly large amount of money.
"All of a sudden their bills started climbing up to...$700 a month," he said.
A fax machine he was promised as part of the deal took eight months to arrive, he said.
Shakib said he eventually became so fed up that he severed ties with Intagr8 but remained locked into a finance agreement until next year.
He wished he had spent more time reading the contracts. "They came at a busy time."
He had been door-to-door to all the car dealers near his business warning them about Intagr8.
Stephen Govinda, who owns the Pacific Foodtown takeaway shop in Glendene, said a friend recommended Intagr8 and he was visited by two salesmen about eight months ago.
"They said all I had to pay was $300 a month for all my calls, that's it. The hardware was all free."
He had two security cameras installed, along with a single phone line (he says he was promised two) and two handsets.
He got a shock when he discovered the $300 was going to a finance company ("I had no idea about them") and was even more surprised when he started getting emails from Intagr8 billing him up to $265 extra a month.
Govinda has cancelled the deal and signed with Vodafone, but is continuing to receive pay demands from the finance company, which is threatening to take him to court and give him a bad credit rating.
"I'm prepared to fight them. We are a very small business, I'm very upset, I don't want to go on the blacklist if I borrow money."
A subcontractor who did about 150 installations for Intagr8 in the Wellington region said its philosophy seemed to be to install equipment as quickly as possible so customer couldn't back out.
The contractor, who asked not to be named, said on occasion he would turn up to businesses and the customer hadn't even signed the contract, or equipment the person had signed for wasn't there.
HOW BUNDLED TELECOMMUNICATIONS SERVICES WORK:
* Customer signs up – documentation includes finance agreement.
* The finance company releases the cash to telco to buy the equipment, which is provided to the customer.
* Customers pay monthly phone bills to telco, which are said to offset most of the rental for the equipment through "call credits". Customers also make regular payments to the finance company.
* The customer is actually locked into a contract with the finance company – typically for a five-year period.
* If the customer terminates the contract with the telco, it still has to pay the finance company for the equipment.
For the Full Article from Blair Ensor and Tony Wall go to http://www.stuff.co.nz/business/industries/71470821/complaints-flood-in-over-telcos-sales-tactics
Phone equipment supplied by Intagr8 and priced at $14,400 over five years was priced by another communications company at $3770 retail. A package priced at $9725 was charged at $51,060 by Intagr8.
Intagr8 denied its hardware was overpriced, saying the products and services it provided were in line with other equipment businesses.
Jay Marshall, of homeware importer EW Sinton, described his dealings with Intagr8 as the worst business experience he'd ever had. He thought the structure of the deals was confusing.
"They make out it's your hardware, but they're getting paid up front for all your projected calling over five years."
UDC Finance, owned by ANZ, declined to comment when asked about Intagr8's business model, the price of its equipment and whether they were aware of customer complaints. .
Joe Duncan, chief executive of finance company Advaro, said they took steps to ensure Intagr8 disclosed sufficient information to its customers and recorded phone calls to ensure people understood what they were getting into.
He said Advaro knew of complaints but thought they'd been resolved. "We are seeking clarification on this."
Grant Maud of Telecom Rentals (now TRL) said they were concerned by the allegations.
Geoff Hamilton of Equipment Finance refused to comment without Intagr8's permission.
She believed she was fired without explanation because she "told them what they didn't want to hear" about their sales techniques.
"If they can keep convincing people to buy the stuff, they'll just keep making money", she said.
Paula Pickles quit her account manager's job at Intagr8 in November after becoming concerned about the way it was operating.
She said salespeople didn't say goods were free but, on the other hand, there was no mention of a finance company.
"People didn't really understand they were signing into a finance agreement – that was my impression."
Another former employee, a technician, said he quit after about two years because he was sick of dealing with angry customers.
"For a communications company there was no communication. It just sucked."
The man, who asked not to be named, said he would often turn up to install phone systems and clients would be furious because they had not received equipment they were already paying for.
Intagr8 said in a statement if customers had issues they should get in touch. "We offer them our assurance that we will make every attempt to remedy any issue they may have."
THE CUSTOMERS
Accroding to Ensor & Wall (2015) "A free computer wasn't enough to entice Crown Cabs owner Khalil Tajek to leave Telecom, but when Intagr8 offered to throw in a "free" printer as well, that sealed it. A year later, Tajek was complaining to the Commerce Commission. He said his agreement was for a monthly bill of $250 plus GST over four years, with that amount given back to him as "credits" to offset the equipment. Shortly after receiving the hardware Tajek got a call from a man at UDC. He said that was the first he knew the gear was on finance.
"The [salesman] did not tell me about this. He just told me to sign some documents, but I did not read them and he did not leave a copy." In the following months, Tajek said, his monthly bills climbed to about $500 as his "credits" only partly offset the finance repayments. Intagr8 said there was no fixed amount for telephone charges – it depended upon usage. Busier periods would result in additional charges. The directors of EW Sinton, a homeware importer, say they effectively lost $50,000 after a "nightmare" experience with Intagr8.They knew a finance company was involved, but say Intagr8 simply failed to deliver what it promised, the equipment not working properly even when they paid more money to get it sorted.Eventually, desperate to escape the problem, they went back to their old phone provider but continued to make their monthly payments on the Intagr8 equipment."
"We were spending so much time on it, we just said 'stuff it' and went to another phone company," said managing director Phil Sinton. "We let the [Intagr8] contract run its course, it cost us about $50,000, basically for nothing."
Haider Shakib, who owns My Auto Tech in Manurewa, remembers the smooth-talking Intagr8 salesmen who arrived in a nice car.
Shakib claimed he was promised "free" phone calls if he bought equipment. He claimed he was told there was no finance component to the five-year deal.
However, monthly letters from a finance company asking for $230 began arriving. He also had to pay Intagr8 an increasingly large amount of money.
"All of a sudden their bills started climbing up to...$700 a month," he said.
A fax machine he was promised as part of the deal took eight months to arrive, he said.
Shakib said he eventually became so fed up that he severed ties with Intagr8 but remained locked into a finance agreement until next year.
He wished he had spent more time reading the contracts. "They came at a busy time."
He had been door-to-door to all the car dealers near his business warning them about Intagr8.
Stephen Govinda, who owns the Pacific Foodtown takeaway shop in Glendene, said a friend recommended Intagr8 and he was visited by two salesmen about eight months ago.
"They said all I had to pay was $300 a month for all my calls, that's it. The hardware was all free."
He had two security cameras installed, along with a single phone line (he says he was promised two) and two handsets.
He got a shock when he discovered the $300 was going to a finance company ("I had no idea about them") and was even more surprised when he started getting emails from Intagr8 billing him up to $265 extra a month.
Govinda has cancelled the deal and signed with Vodafone, but is continuing to receive pay demands from the finance company, which is threatening to take him to court and give him a bad credit rating.
"I'm prepared to fight them. We are a very small business, I'm very upset, I don't want to go on the blacklist if I borrow money."
A subcontractor who did about 150 installations for Intagr8 in the Wellington region said its philosophy seemed to be to install equipment as quickly as possible so customer couldn't back out.
The contractor, who asked not to be named, said on occasion he would turn up to businesses and the customer hadn't even signed the contract, or equipment the person had signed for wasn't there.
HOW BUNDLED TELECOMMUNICATIONS SERVICES WORK:
* Customer signs up – documentation includes finance agreement.
* The finance company releases the cash to telco to buy the equipment, which is provided to the customer.
* Customers pay monthly phone bills to telco, which are said to offset most of the rental for the equipment through "call credits". Customers also make regular payments to the finance company.
* The customer is actually locked into a contract with the finance company – typically for a five-year period.
* If the customer terminates the contract with the telco, it still has to pay the finance company for the equipment.
For the Full Article from Blair Ensor and Tony Wall go to http://www.stuff.co.nz/business/industries/71470821/complaints-flood-in-over-telcos-sales-tacticsTelstraClear Ltd Fraud Department warning – PABX fraud/hacking
Posted by sam in PABX Systems | 0 comments

Fraud Department Warning | Telephone System Security Guidance In discussion recently held with some of the other large Telco’s in New Zealand it was found that a number of businesses in New Zealand had been hit lately with PABX fraud/hacking. While this type of fraud has been around for a very long time now it seems that the would-be fraudsters are now back trying to hit businesses in New Zealand. In most cases PABX fraud can be avoided if the customer speaks with their PABX, and / or voicemail vendor, and requests that one or both facilities be audited to check for potential fraud weaknesses. PABX fraud has been occurring throughout the world for the past 10-20 years. The types of fraud perpetrated on our customers are usually nothing new, and often have previously occurred elsewhere in the world. New Zealand based PABX, and voicemail, vendors therefore should be well aware of the types of telecommunications fraud their product is vulnerable to, and should be able to apply permanent fixes to their respective product/s if an audit shows them to be insecure.
PABX Fraud (Private Automatic Branch Exchange)
What is PABX Fraud?
A PABX is a computerised system that manages an internal telephone extensions network. It is a highly flexible system in that it can, if necessary, provide access to telephone services by dialing into the system from outside the PABX network. This service is called DISA (Direct Inwards System Access) and, if enabled, it permits employees to route national and international calls through the PABX with the cost of these calls being billed to the owner of the PABX. Access to this service requires the use of a PIN, however, this can be abused and may result in unauthorised calls costing thousands of dollars. Most PABX’s have engineering and maintenance access codes. If this access code is compromised the attacker will have total control of the system. NOTE: There is a large amount of information on the Internet relating to toll fraud, PABX fraud, etc. Go to Google and use the word PABX to find useful information about this type fraud.How will I know if my PABX has been a victim of PABX Fraud?
If your PABX has voicemail and is DISA enabled then it is susceptible to this form of fraud. Usually, the only indication that you will see is a substantial increase in your telephone bill. Detailed billing will assist in identifying any potential unauthorised calls, usually International calls but they can also be National and mobile telephone calls. Another indicator is where customers trying to dial in or employees trying to dial out, find that the lines are always busy. Audit your bill each month:- Check your bill regularly and ensure you can account for all itemised calls
- Look for calls to international countries that you wouldn’t normally be doing business with.
- Look for calls being made outside of your business hours.

How can I protect my PABX from this type of fraud?
If DISA is not required ensure that it is disabled. If it is required, the people who supplied, or who are maintaining your system, understand the full functionality of the PABX and they can help in configuring DISA properly. If automatic logging of calls is available, enable it. It may help in identifying the extension number being used to compromise the PABX and it may also identify the source of the external call. Regularly check the log records for repeated short duration calls to the same number. This could be an indication of an attempt to attack your system. PIN’s for voicemail, DISA and engineering access should, if enabled, be activated and changed regularly. If possible engineering access should only be permitted on a ‘call back’ basis; this will prevent unauthorised access to this privileged account.Prevention Strategies
- Never give out technical information about your system to callers - unless you are certain who is on the other end of the line.
- Do not allow your system administrator to maintain factory set passwords for maintenance of your system.
- Introduce a PIN and password management policy where employees are not permitted to use predictable PIN numbers such as the last digits of their DDI, sequential numbers like 1111, 0000, or incremental numbers like 1234.
- Ensure that PIN numbers are changed regularly, and supervisor and maintenance passwords are changed when the administrator, an employee, or a contractor leaves the business.
- Do not place a list of all your staffs names and contact numbers on your website or out on the Internet. You are providing the would-be fraud offenders with a list of all your company phone numbers that they can now try to hack into.
- Do not allow unlimited unsuccessful attempts to enter voicemail - configure the system so that 3 unsuccessful attempts results in call failure.
- Disable an administrator, contractor or employee's mailbox account when he or she leaves your company.
- Schedule regular PABX checks with your maintainer and form a regular risk mitigation strategy to limit any system vulnerabilities.
- Ensure that your PABX room is locked when not attended.
- Be alert to the overt signs of PABX fraud such as repeated calls of short duration, high numbers of inbound hang-up calls, unexplained increases in incoming calls where the caller hangs-up when answered, sudden increases in national and international usage, or changes in after-hours calling patterns or calls to unknown overseas numbers or countries.
PABX Fraud Frequently Asked Questions
- When I get hacked, who is going to pay for the calls? Your company is responsible for all charges incurred on your system not the carrier, the responsibility for the security of your PABX system is yours and you should take steps to protect your assets.
- Who are these people and why are they stealing calls? Today, highly skilled, technologically sophisticated criminals who have little fear of being detected, let alone apprehended or prosecuted perpetrate communication theft from remote distances. These criminals conduct a growing business selling access to communications systems all over the world.
- Why don't the carriers write off these charges? Today, fraudulent calls are placed over many different inter-exchange Carriers (IXC); each carrier must pay that portion of the call handled by them. When the call is placed to an international location the domestic carrier must pay the foreign carrier regardless of the fraud. You the end user control access to your PABX system not your telecommunication provider so you are responsible for the charges incurred.
- Why is identifying or stopping the fraudulent calls the customer's responsibility? Only the customer can differentiate legitimate calls from fraudulent ones. The carriers do not have access or permission to work on your PABX, the vehicle that hackers use most to conduct their activities.
- How will the hacker find my system? Criminals pay for a PABX maintenance port number and password. Hackers 'scan' using auto-diallers to find systems equipped with modems. Your Company's telephone directory listing or your 0508 / 0800 service advertising make you known to the hacker.
- How do I justify the expense of corrective action when we have not suffered a loss? Past performance is not an accurate indicator of present threats. The equipment and the motivation to perpetrate this criminal activity did not exist years ago. Educate your managers about the pitfalls of not protecting your Corporate assets and enlist their support by implementing a Corporate policy on unauthorized access as your first step.
- How does a hacker gain access to my system? Hacker’s use computerized calling programs, automatic diallers, and sophisticated software to break your systems security and pass codes. Hackers attempt to gain access in the following order:Phone Mail / Voice Mail 2) Automated Attendant 3) Remote Access or Direct Inward Service Access (DISA) 4) Remote Maintenance/ Administration Port.
- Why is it important to protect my Maintenance/Administration Port? This is the most important port on your PABX system. Hackers gain access to your system software and control your Voice Mail, DISA and other PABX features through the maintenance port.
- How do hacker know which CBX / PBX type and brand of Voice Mail I am using? Hackers identify the type of PABX by the Login procedure used for each system. They know the pass codes for each vendor PABX. Hackers also recognize the various Voice Mail and Phonemail systems by the default digitized voice recordings.
- How does a hacker use my Voice Mail? Through your Voice Mail the hacker is able to use your PABX "trunk-to-trunk connections" feature to access your long distance network. 2) Your Voice Mail might also be used as a "bulletin board" to distribute stolen credit card and other hacker related information. 3) They may change your greeting to "Hello!...pause....Yes, I'll accept the charges to Zaire."
- I understand why a larger user must be concerned, but I'm a small business / or in a rural community. Why should hacker activity concern me? Hackers use auto-diallers to search entire area codes to find systems to hack, they do not care who or where their victims are. No one is safe, and smaller companies may be less able to absorb the average loss ranging from $10,000 to $100,000.00 plus dollars per incident.
- What happens when a hacker finds my Maintenance / Administration Port? Hackers use manufacturers default passwords or computer generated, craker programs until they find a usable password. They then enter a system unlawfully and make software changes that allow unauthorized calls. Information on how to use your altered system is then sold to "call sell operators" who sell calls over your system to whomever wishes to place calls. These calls are typically made from public telephones (pay phones) in large metropolitan cities.
- What is different about this theft from other forms of fraudulent activity? There are three major differences with this case: The call is processed as data, not voice. An international organization is required to: find the victim, set up the call, collect the money and manage the administration in a foreign location. The theft or scheme has migrated and expanded in form and severity.
- What can we do to protect ourselves from these crooks and con artists? As with your personal lives, the better informed you are to the risks the better protected you are. Stay on top of the current threats (visit scamwatch.govt.nz), add policy on security, secure your system configuration, set-up a team approach to security and service & work with your equipment vendor. Do not let management or your Company be taken by surprise. This is one disaster that is very predictable and equally preventable.
Health and Safety Update, Training and Software Rollout
Posted by sam in Uncategorized | 0 comments
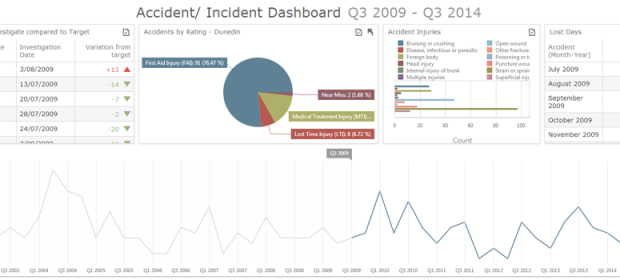
We would like to congratulate four of our staff for recently completing Site Safe Supervisor Gold Card training. As well as helping with proactively managing safety on site, the two day course covered accident investigation and hazard analysis. This extends our existing capabilities in this area and ensures that our project managers are fully up to speed with the latest safety management methods and processes. The company is also pleased to announce the rollout of Safety Manager throughout the business. Training begins at the end of April and we expect to have the system fully operational by the end of May. A dedicated project team has been set up to migrate the existing paper based system into Safety Manager. This software will enable us to report incidents directly into the system via a tablet app from the field, with follow up investigation reports and corrective actions also being stored within the system. It also provides a repository for training records, hazard analysis and other compliance information as well as providing a tool for the creation of job safety analyses. Safety Manager enables us to demonstrate compliance with new health and safety legislation and ACC programme requirements, all in line with our goal of becoming ACC Tertiary accredited and positioning ourselves as a low risk, self-managing contractor”.
PABX Fraud
Posted by sam in PABX Systems | 0 comments

In discussion recently held with some of the other large Telco’s in New Zealand it was found that a number of businesses in New Zealand had been hit lately with PABX fraud/hacking. While this type of fraud has been around for a very long time now it seems that the would-be fraudsters are now back trying to hit businesses in New Zealand. In most cases PABX fraud can be avoided if the customer speaks with their PABX, and / or voicemail vendor, and requests that one or both facilities be audited to check for potential fraud weaknesses. PABX fraud has been occurring throughout the world for the past 10-20 years. The types of fraud perpetrated on our customers are usually nothing new, and often have previously occurred elsewhere in the world. New Zealand based PABX, and voicemail, vendors therefore should be well aware of the types of telecommunications fraud their product is vulnerable to, and should be able to apply permanent fixes to their respective product/s if an audit shows them to be insecure.
PABX Fraud (Private Automatic Branch Exchange)
What is PABX Fraud?
A PABX is a computerised system that manages an internal telephone extensions network. It is a highly flexible system in that it can, if necessary, provide access to telephone services by dialing into the system from outside the PABX network. This service is called DISA (Direct Inwards System Access) and, if enabled, it permits employees to route national and international calls through the PABX with the cost of these calls being billed to the owner of the PABX. Access to this service requires the use of a PIN, however, this can be abused and may result in unauthorised calls costing thousands of dollars. Most PABX’s have engineering and maintenance access codes. If this access code is compromised the attacker will have total control of the system. NOTE: There is a large amount of information on the Internet relating to toll fraud, PABX fraud, etc. Go to Google and use the word PABX to find useful information about this type fraud.How will I know if my PABX has been a victim of PABX Fraud?
If your PABX has voicemail and is DISA enabled then it is susceptible to this form of fraud. Usually, the only indication that you will see is a substantial increase in your telephone bill. Detailed billing will assist in identifying any potential unauthorised calls, usually International calls but they can also be National and mobile telephone calls. Another indicator is where customers trying to dial in or employees trying to dial out, find that the lines are always busy. Audit your bill each month:- Check your bill regularly and ensure you can account for all itemised calls
- Look for calls to international countries that you wouldn’t normally be doing business with.
- Look for calls being made outside of your business hours.
How can I protect my PABX from this type of fraud?
If DISA is not required ensure that it is disabled. If it is required, the people who supplied, or who are maintaining your system, understand the full functionality of the PABX and they can help in configuring DISA properly. If automatic logging of calls is available, enable it. It may help in identifying the extension number being used to compromise the PABX and it may also identify the source of the external call. Regularly check the log records for repeated short duration calls to the same number. This could be an indication of an attempt to attack your system. PIN’s for voicemail, DISA and engineering access should, if enabled, be activated and changed regularly. If possible engineering access should only be permitted on a ‘call back’ basis; this will prevent unauthorised access to this privileged account.Prevention Strategies
- Never give out technical information about your system to callers - unless you are certain who is on the other end of the line.
- Do not allow your system administrator to maintain factory set passwords for maintenance of your system.
- Introduce a PIN and password management policy where employees are not permitted to use predictable PIN numbers such as the last digits of their DDI, sequential numbers like 1111, 0000, or incremental numbers like 1234.
- Ensure that PIN numbers are changed regularly, and supervisor and maintenance passwords are changed when the administrator, an employee, or a contractor leaves the business.
- Do not place a list of all your staffs names and contact numbers on your website or out on the Internet. You are providing the would-be fraud offenders with a list of all your company phone numbers that they can now try to hack into.
- Do not allow unlimited unsuccessful attempts to enter voicemail - configure the system so that 3 unsuccessful attempts results in call failure.
- Disable an administrator, contractor or employee's mailbox account when he or she leaves your company.
- Schedule regular PABX checks with your maintainer and form a regular risk mitigation strategy to limit any system vulnerabilities.
- Ensure that your PABX room is locked when not attended.
- Be alert to the overt signs of PABX fraud such as repeated calls of short duration, high numbers of inbound hang-up calls, unexplained increases in incoming calls where the caller hangs-up when answered, sudden increases in national and international usage, or changes in after-hours calling patterns or calls to unknown overseas numbers or countries.
- When I get hacked, who is going to pay for the calls? Your company is responsible for all charges incurred on your system not the carrier, the responsibility for the security of your PABX system is yours and you should take steps to protect your assets.
- Who are these people and why are they stealing calls? Today, highly skilled, technologically sophisticated criminals who have little fear of being detected, let alone apprehended or prosecuted perpetrate communication theft from remote distances. These criminals conduct a growing business selling access to communications systems all over the world.
- Why don't the carriers write off these charges? Today, fraudulent calls are placed over many different inter-exchange Carriers (IXC); each carrier must pay that portion of the call handled by them. When the call is placed to an international location the domestic carrier must pay the foreign carrier regardless of the fraud. You the end user control access to your PABX system not your telecommunication provider so you are responsible for the charges incurred.
- Why is identifying or stopping the fraudulent calls the customer's responsibility? Only the customer can differentiate legitimate calls from fraudulent ones. The carriers do not have access or permission to work on your PABX, the vehicle that hackers use most to conduct their activities.
- How will the hacker find my system? Criminals pay for a PABX maintenance port number and password. Hackers 'scan' using auto-diallers to find systems equipped with modems. Your Company's telephone directory listing or your 0508 / 0800 service advertising make you known to the hacker.
- How do I justify the expense of corrective action when we have not suffered a loss? Past performance is not an accurate indicator of present threats. The equipment and the motivation to perpetrate this criminal activity did not exist years ago. Educate your managers about the pitfalls of not protecting your Corporate assets and enlist their support by implementing a Corporate policy on unauthorized access as your first step.
- How does a hacker gain access to my system? Hacker’s use computerized calling programs, automatic diallers, and sophisticated software to break your systems security and pass codes. Hackers attempt to gain access in the following order:Phone Mail / Voice Mail 2) Automated Attendant 3) Remote Access or Direct Inward Service Access (DISA) 4) Remote Maintenance/ Administration Port.
- Why is it important to protect my Maintenance/Administration Port? This is the most important port on your PABX system. Hackers gain access to your system software and control your Voice Mail, DISA and other PABX features through the maintenance port.
- How do hacker know which CBX / PBX type and brand of Voice Mail I am using? Hackers identify the type of PABX by the Login procedure used for each system. They know the pass codes for each vendor PABX. Hackers also recognize the various Voice Mail and Phonemail systems by the default digitized voice recordings.
- How does a hacker use my Voice Mail? Through your Voice Mail the hacker is able to use your PABX "trunk-to-trunk connections" feature to access your long distance network. 2) Your Voice Mail might also be used as a "bulletin board" to distribute stolen credit card and other hacker related information. 3) They may change your greeting to "Hello!...pause....Yes, I'll accept the charges to Zaire."
- I understand why a larger user must be concerned, but I'm a small business / or in a rural community. Why should hacker activity concern me? Hackers use auto-diallers to search entire area codes to find systems to hack, they do not care who or where their victims are. No one is safe, and smaller companies may be less able to absorb the average loss ranging from $10,000 to $100,000.00 plus dollars per incident.
- What happens when a hacker finds my Maintenance / Administration Port? Hackers use manufacturers default passwords or computer generated, craker programs until they find a usable password. They then enter a system unlawfully and make software changes that allow unauthorized calls. Information on how to use your altered system is then sold to "call sell operators" who sell calls over your system to whomever wishes to place calls. These calls are typically made from public telephones (pay phones) in large metropolitan cities.
- What is different about this theft from other forms of fraudulent activity? There are three major differences with this case: The call is processed as data, not voice. An international organization is required to: find the victim, set up the call, collect the money and manage the administration in a foreign location. The theft or scheme has migrated and expanded in form and severity.
- What can we do to protect ourselves from these crooks and con artists? As with your personal lives, the better informed you are to the risks the better protected you are. Stay on top of the current threats (visit scamwatch.govt.nz), add policy on security, secure your system configuration, set-up a team approach to security and service & work with your equipment vendor. Do not let management or your Company be taken by surprise. This is one disaster that is very predictable and equally preventable.
PABX Fraud Frequently Asked Questions
Remember that you will be a victim and that you and only you control the severity of these attack. Hackers and Phreakers are much easier to stop from breaking in than they are to evict.Ministry of Education Project
Posted by sam in CCTV, Cloud Communications, Fibre Optic, PABX Systems | 0 comments




